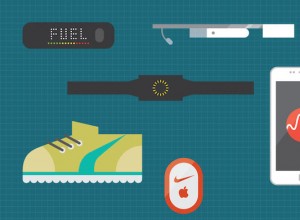
These days, wearable products are the talk of the town. Many believe wearable products will lead to the decline of the smartphones in the upcoming years. However in fact, this technology will only make the smartphone more central to our lives and here is why.
Blog
Trillion dollar battery breakthrough is still a dream for electric car companies
Tesla and Nissan are the two major car companies that have fully invested in the electric car future. Tesla made it to the top with its Model S sedan that runs fully electric. Its CEO Elon Musk is a serial entrepreneur, and according to his previous profile in investment he sees the future better than […]
US defense vendors invaded by Iranian hackers this week
Cyber-espionage is not anymore hypothetical, it is happening already, and the wrath of its claws has been felt no more palpably than by the major defense contractors to the US government. The culprit: a hacking group from Iran.
Apple faces class action suit over missing iMessages sent to non-iOS devices
It facetiously looks queer, even unlikely, that your text message should appear as delivered on your iPhone or iPad but actually did not reach the intended recipient who has ditched his or her iOS device for an Android toting gadget.
Will the iPhone 6 finally support NFC technology?
The past few weeks have been an outpouring of rumors about the upcoming iPhone 6 – its new features, highlights and everything that would make it retain the luster that the iPhone family is known for. So far, nothing can be confirmed from those reports.
Google appoints Marketing Executive Ivy Ross as head of Google Glass
Google has started selling its Google Glass to anyone with the money ($1500) in the United States. Being available to the general public puts a lot of pressure on Google to make its product successful. Google has made some major HR changes at Google Glass division.