Ransomware is just another form of data and money extortion that happens online, and it is taking Internet users by storm. But no matter what, you should not give in to the demands of cyber criminals looking to cash in on your data.
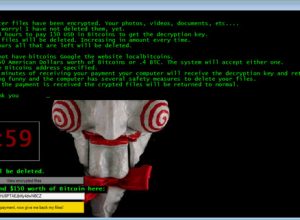
Download this Tool if you are a Victim of the Jigsaw Ransomware
Security experts at BleepingComputer(dot)com were quick to provide a solution to decrypt a new ransomware aptly called Jigsaw which not only encrypts your most precious computer files, but also deletes them incrementally if you do not pay the ransom.
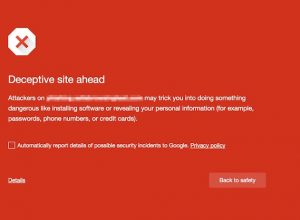
Did Google’s anti-social engineering campaign live up to its promise?
How does Google crack down on websites with deceptive advertisements and buttons? Let us count the ways. More than two months after Google expanded its effort to help keep Internet users safe from social engineering attacks – the sort of fraudulent ads and “Download and Play” button you see on your favorite video streaming site […]
Beware of a new phishing scheme targeting Apple ID users
There are many reasons why scammers continue to thrive, one of which is that many mobile and Internet users also continue to believe in their tactics. The attackers’ targets vary from online credentials to bank accounts.
Will BlackBerry’s plan to launch two Android devices make or break the firm?
BlackBerry might be facing a decisive moment, its final chance, to save the ailing business later this year as the company plans to introduce two new handsets that will run the Android mobile operating system instead of its own proprietary BB10.
How to minimize the attack surface for ransomware
Not a week has passed without the frequent headlines of ransomware attacks hitting various sectors – from private companies to hospitals. The list could, in fact, be unending. Clearly, the rise of ransomware attacks seems to know no boundary, and the very least that we could do is to help minimize the attack surface for […]