Assuming that legal professionals are unable to embrace technology is often exaggerated. Although they have never been at the helm of tech innovation, it has undoubtedly changed the way they practice law – for the better.
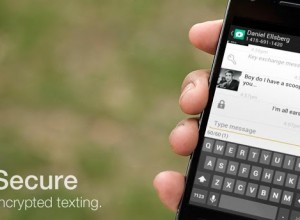
TextSecure no longer encrypts your SMS, what to do?
Following the revelations of Edward Snowden on a surveillance program run by the National Security Agency to spy on individuals’ online activities and communication, a host of SMS encryption services became an in-demand product. But TextSecure, one of the pioneers in this area, is dropping support for encrypted text messages.
Cryptocurrency mining software forcibly installed in computers of uTorrent users
If you are using uTorrent to download files from the Internet, chances are that your computer might have been infected with a cryptocurrency mining software, a kind of bloatware that steals bitcoins and other digital currencies from a computer.
Adobe kicks off vulnerability disclosure program without incentives
We have seen the rise of bug bounty programs in many large tech companies as a result of the growing threat landscape that, if unchecked, would bring tremendous damage to critical infrastructures and businesses.
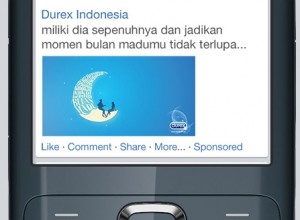
Facebook is cashing in on slow Internet speed
You may think of Facebook as scrambling all too hurriedly to deliver high-speed Internet to potential users in emerging economies with the Internet.org project, but there’s something in slow speed that gets the social networking site hooked to snail pace mobile browsing.
Xiaomi Mi 4 device pre-installed with malware, security test shows
Chinese phone manufacturer Xiaomi may be enjoying warm market embrace with the exponential growth in Mi 4 sales, but that might change following discovery of malware that has been allegedly preinstalled in the device.