Two security vendors, Symantec and Kaspersky Labs, have discovered two apps on Google Play this week that, out of the users’ confidence that they truly are security apps meant to scan a device for malware, have encrypted the devices for a ransom.
Researchers from Symantec found that Simplocker is one of those apps that maliciously encrypt devices after putting on a false disguise that it is there as a legitimate app for security. In reality, it operates in the background encrypting all files on your device and eventually locking up your handset to demand later for money as payment for the key to your smartphone.
The Simplocker app finds wide popularity among the Russian-speaking countries, where users see a full-screen message on their handsets saying their phones have been locked for visiting a child pornography site (which may or may not be true from user to user). This happens after the app completes installation on the phone in the background. As in any ransomware scheme, the app asks for hundreds of dollars for the user to regain back the encrypted files on the device and the handset itself.
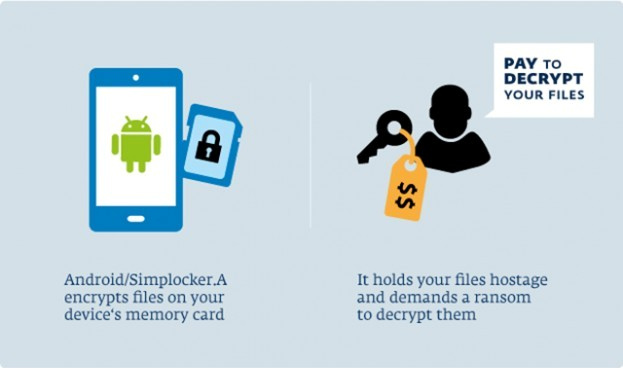
Simplocker encrypts almost all files stored on the device and within memory cards, such as videos with file types .3gp and .avi, word documents of the type .doc, .txt, and .docx, photos with name extensions .gif, .jpeg, .png and .jpg, music files, and portable documents like PDF.
It was the first case that a ransomware targeted to Android devices has been spotted with confirmation from researchers.
Read also: A wave of old ransomware targeted Android devices this week
Users who may have already installed the app can resort to simple steps of preventing the app from infecting your phone by immediately shutting down the device and rebooting to uninstall it, provided the device still is free from being locked up. In case the app was able to already lock up the smartphone, users can reboot their handsets to safe mode in order to block third-party apps from starting up and only the basic features of the device would run. By then, the Simplocker ransomware can be uninstalled.
Kaspersky Lab also reported about Pletor, which is being sold in underground markets for $5,000 and he ransomware counts more than 2,000 infected devices also in Russia and in Ukraine. Pletor infects smartphones of users who may have previously visited porn sites, as in the case of Simplocker. Pletor disguises itself as a media player and less wary users who would open media files using Pletor are sure to run the risk of getting their devices locked up in the bewilderment of ransom scheme.
Users only have to remember to shun apps from third-party sites as they are never safe.



