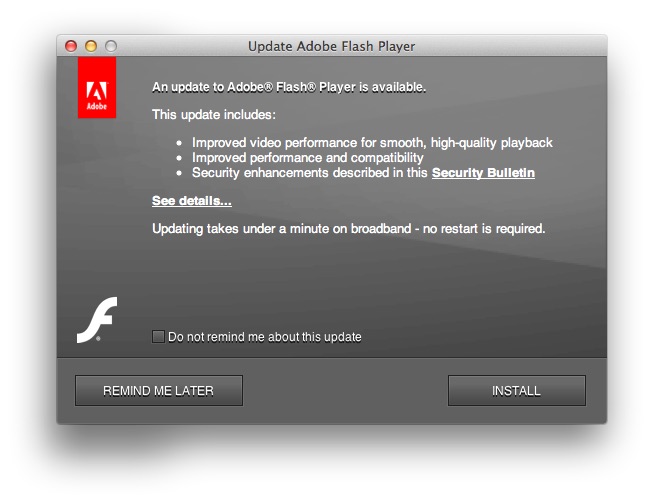
Apple prides itself in having a robust security infrastructure for customers. But a recent fake Adobe Flash Player update was able to slip past its security radar and infected a number of Mac computers after the users were deceived into believing that the software update came from Adobe itself.
Security experts at Intego were the first to discover the rogue update, which in fact was a variant of OSX/InstallCore that spreads in the wild as a Mac Package installer. The curious thing about it is that the installer has been signed with a legitimate Developer ID certificate, issued by Apple to its developers in order to qualify their products into the Apple App Store.
The presence of the Developer ID certificate was the main reason the Mac OS X Gatekeeper was made to trust in the otherwise rogue installer. Following installation of the update, Mac users began to see a proliferation of unwanted programs in their computers such as those detected by Intego researchers. These include the MacKeeper, ZipCloud and MegaBackup, third-party applications that otherwise would not be allowed by Apple to get their way into the OS X ecosystem had there not been a legitimate Developer ID certificate.
There was an earlier version of the OSX/InstallCore that Intego also spotted in the wild, which led to the spread of a scareware after Mac users fell for the same deceptive tactic exploiting a fake Adobe Flash update. As in the case with the present rogue installer, the previous OSX/InstallCore was also signed with a Developer ID certificate, which made the update look legitimate to Mac Gatekeeper.
As a sort of security measure imposed by Apple on all Mac users, applications that do not come from its official app store will be blocked from the OS X ecosystem in order to help malicious code from spreading in the computer. But if an attacker is able to possess an Apple developer certificate, that’s the time when your Mac computer could be at risk of being infected with malware because it will download and install a rather malicious app, believing it is legitimate and can be trusted.
The OS X Gatekeeper security protocol is not at all free from flaws. There are inherent vulnerabilities in the system that sometimes allows malicious code to get its way onto the Mac computer, but the use of a valid Apple developer certificate seems to be the easy way for many hackers, and one that Apple has yet to turn its eyes to.
It could be that some Apple developers have been negligent in handling their own certificate that they might have exposed it to cyber crooks. Which highlights the need to remind those developers that they, too, must observe some security practices.
Disclosure: We might earn commission from qualifying purchases. The commission help keep the rest of my content free, so thank you!