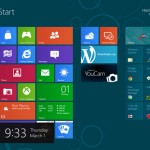
In the previous versions of the Windows Operating Systems, you could modify or access to various settings of your system using the applications in Control Panel. Microsoft’s latest operating system, Windows 8 is supported by the Metro User Interface. You would still find the Control Panel in the desktop mode of the OS, but a […]
News
Best Gadgets for Travelling in 2012
Today there are loads of gadgets which are available in the market. Each one has futuristic aptitude. Choosing from thousands of such gadgets is a difficult task. What poses even a bigger challenge is accessing these gadgets while travelling. You might be scuba diving or trekking. Using your iPad or iPhone may not be a […]
The Blogger’s Guide to Interviewing
One of the best things about blogging is interviewing. It is a time when something as casual as a conversation can make for a great article piece. However, as casual as it may be, interviewing is by no means simple on the first try. It takes practice to not only gain good interviewing skills, but […]
Does Page Rank Actually Matter?
PageRank gets a lot of press in the world of SEO, no one can deny that fact. After all, there are a lot of different sites that are dedicated to the idea of your PageRank. After all, when you look at its definition a Page Rank sounds like it would be important:
Best Lightweight Linux Distribution for Older Computers
The development of technology is very dynamic. Therefore, you always need to keep pace with this upgraded technology. The statement goes well in the case of computers. As soon as you get a computer, you need to update the system frequently. It is not possible for any one to get a new one in every […]
Five Ways You Can Optimize Your Blog – Right Now!
When you find that your blog hits a rut in viewers, it can be bad for bloggers who aren’t prepared. For those who aren’t, they can find their blog becoming victim to this dip in viewers or content. This can make the blogger feel less confident about their work and blog. However, there are many […]