CryptoLocker is out, Kovter is in.
The old police ransom malware is making a comeback after long years of dormancy, according to findings by security researchers. The Kovter police blackmail Trojan was perhaps in existence since the formative days of ransomware in 2011, though it slipped off our consciousness when the more sophisticated malware of this sort began to make headway.
Security researchers from Damballa, however, found that a fresh Kovter grew in persistence from May to June this year, sparking fears that the old, yet formidable ransomware is returning with more spiteful attacks this time. The security firm detected at least 25,000 hits in May and 38,000 in June. Worse, it is expected to reach hundreds of thousands of hits in just a span of weeks.
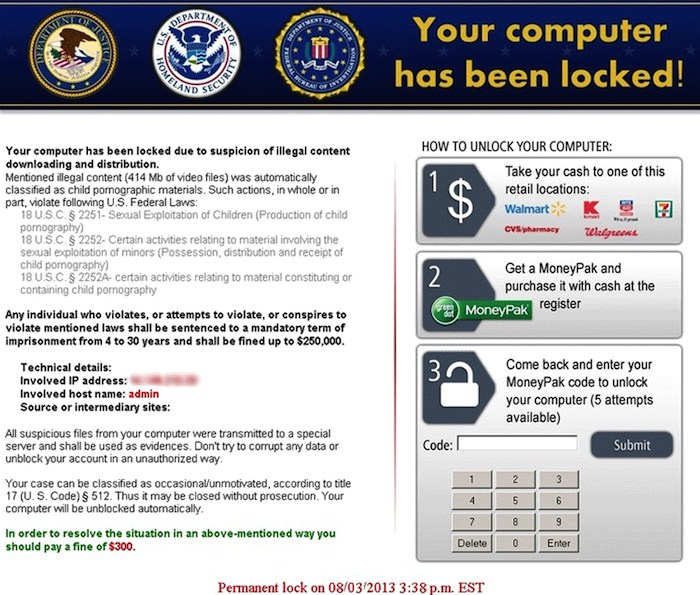
Unlike the complex composition of more advanced ransomware such as CryptoLocker, which was reportedly busted recently by the FBI and its international counterparts, Kovter is devoid of all those complexities.
Kovter operates in much the same way as other police ransom and extortion Trojan do. First, it tries to lure users into making payment to regain control of their locked devices. On top of that, it would also warn users for purportedly viewing pornographic sites. The ransomware does this by tracking the Web browsing history of a certain target computer. This is of course an obvious attempt to raise alarm among users and disturb their psyche in order to coerce them into making the payment, mostly ranging up to $1,000. But the malware of course does not stop even after payment has been made.
And to escalate the convincing power of a fake message to be displayed for the target victims, Kovter works to customize the content based on the data that it could potentially find from the computer’s system.
Security experts are still unable to determine the driving force behind the growing number of incidents of this malware. It could be that the hopes of attackers have been dampened by the FBI’s recent busting of more modern ransomware, so they are turning to the old-school techniques to carry on with their business as usual.
According to Damballa researchers, there is not much that the malware can do at present since more advanced anti-malware methods are currently in place and current best practices still work to address these threats.
The company calls on the security community to collaborate and join forces in order to stop the ransomware from growing into an uncontainable threat.



